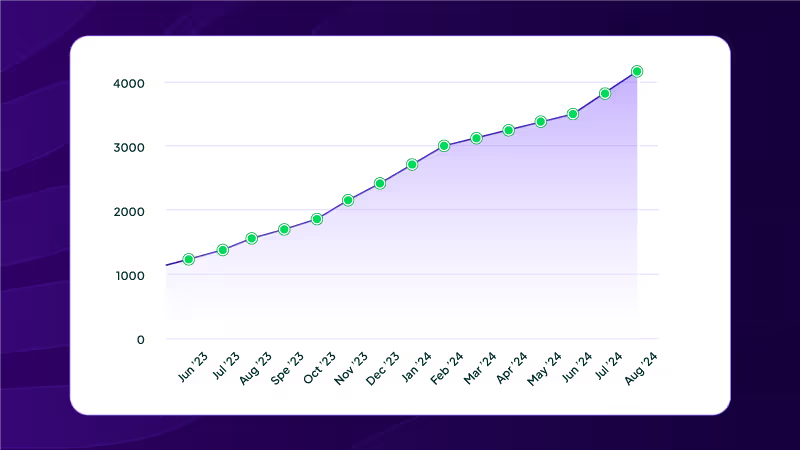
We are thrilled to announce another significant milestone in our journey to enhance CI/CD security across the open-source ecosystem: StepSecurity Harden-Runner now secures over 4,000 repositories on GitHub! This achievement comes just over two months after reaching our 3,500 repositories milestone in June 2024, demonstrating the rapidly growing adoption of Harden-Runner in the developer community.
The Rising Threat of CI/CD Supply Chain Attacks
This milestone comes at a crucial time, as we've witnessed a sharp increase in CI/CD supply chain attacks. Recent events have underscored the critical need for robust security measures in CI/CD pipelines:
1. BlackHat 2024 Presentation: Security researchers Adnan Khan and John Stawinski delivered an eye-opening presentation at BlackHat 2024, detailing the evolving tactics of attackers targeting CI/CD pipelines. Their research highlighted the sophistication of these attacks and the potential for widespread impact.
2. Stripe Public Repository Incident: In a recent incident, a supply chain attack was detected in one of Stripe's public repositories. This event served as a stark reminder that even well-resourced organizations can fall victim to these attacks, emphasizing the need for vigilant security practices in open-source projects.
These incidents, among others, underscore the growing importance of solutions like Harden-Runner in safeguarding the software supply chain.
Why Developers Choose Harden-Runner
StepSecurity Harden-Runner continues to be the go-to solution for network egress control and CI/CD infrastructure security in GitHub Actions environments. Its adoption by major players such as Microsoft, Google, CISA, DataDog, Intel, and hundreds of other organizations speaks volumes about its efficacy and reliability.
Key Benefits
1. Exfiltration Prevention: Harden-Runner monitors and blocks egress traffic at the DNS and network layers, preventing the exfiltration of source code and sensitive CI/CD secrets.
2. Build Tampering Detection: It detects any attempts to tamper with source code or build artifacts during the build process, safeguarding against supply chain attacks.
3. Real-time Monitoring: Continuous monitoring of file and network operations during CI/CD pipeline execution helps identify unusual activities promptly.
4. Anomaly Detection: By establishing a baseline of expected build behavior, Harden-Runner can flag potential anomalies and new outbound destinations.
5. Detailed Insights: Comprehensive reports provide visibility into the build process, helping pinpoint the exact nature and source of any issues.
Recent Enhancements
Since our last milestone, we've continued to improve Harden-Runner with new features to better serve our growing user base:
1. Advanced Process Tracking: We've significantly enhanced our process tracking capabilities. Harden-Runner now provides detailed visibility into processes that make network calls or perform file write operations during the build process. This includes:
- Viewing process names and their arguments
- Displaying the full process tree to understand the hierarchy and relationships between processes
- Correlating processes with specific network and file activities
These improvements provide deeper insights into the execution flow, helping to identify any unexpected or potentially malicious processes and their activities.
2. Support for ARM Runners: Recognizing the growing popularity of ARM-based systems, Harden-Runner now fully supports ARM runners. This expansion ensures that teams using ARM architecture in their CI/CD pipelines can benefit from the same level of security and monitoring.
Looking Ahead
As we celebrate this 4,000+ repositories milestone, we're more committed than ever to expanding our reach and capabilities:
- Insights Page UI Revamp: We're excited to announce that we're currently revamping our insights page UI to make it simpler and more intuitive. This update will enhance user experience, making it easier for you to navigate and understand the security insights provided by Harden-Runner.
- Improved Documentation: We're working on comprehensive improvements to our documentation. Our goal is to provide clearer, more detailed guides and explanations to help users get the most out of Harden-Runner's features and capabilities.
- Platform Expansion: We're actively working on extending Harden-Runner support to GitLab, BitBucket, Azure DevOps, and Harness.
- Continuous Improvement: We're constantly refining our anomaly detection and monitoring capabilities to stay ahead of emerging threats.
- Community Engagement: We're deepening our engagement with the open-source community to gather feedback and ensure Harden-Runner meets the evolving needs of developers.
Project Spotlight: Carbon Lang
As we celebrate this milestone, we're proud to highlight how leading open-source projects are leveraging Harden-Runner to enhance their security. One notable example is Carbon Lang, an experimental successor to C++, which has over 32,000 stars on GitHub.
Carbon Lang recently adopted Harden-Runner, implementing robust security measures across their workflows. Here's how they're using it:
1. Comprehensive Implementation: Carbon Lang has integrated Harden-Runner into most of their workflows, demonstrating a commitment to securing their entire CI/CD pipeline.
2. Strict Block Policies: The project has set up block policies for the majority of their workflows, limiting network access to only necessary endpoints. This significantly reduces the attack surface for potential supply chain attacks.
3. Transparent Security Practices: Carbon Lang has updated their README to include a dedicated "Hardening" section, which explains their use of StepSecurity tools and provides links to their Harden-Runner findings.
This implementation by Carbon Lang serves as an excellent example of how projects can leverage Harden-Runner to significantly enhance their CI/CD security. Their approach not only secures their own project but also sets a standard for security best practices in the open-source community.
You can see Carbon Lang's implementation of Harden-Runner in this pull request: https://github.com/carbon-language/carbon-lang/pull/4192/files

Join the Secure CI/CD Movement
If you haven't yet implemented Harden-Runner in your GitHub Actions workflows, now is the perfect time to join the thousands of developers, including those behind projects like Carbon Lang, who are already benefiting from enhanced CI/CD security. Let us help you secure your repositories against supply chain attacks while you focus on building amazing software!
Thank you to all the developers and organizations who have placed their trust in StepSecurity Harden-Runner. Here's to securing the next 4,000 repositories and beyond!
To get started with Harden-Runner or learn more about how it can enhance your CI/CD security, visit StepSecurity's website or check out the Harden-Runner GitHub repository.

.png)

.png)
