We are thrilled to announce that StepSecurity Harden-Runner has now secured over 3500 repositories on GitHub! This milestone comes just under two months after the previous milestone of 3000+ repositories secured with Harden-Runner. The milestones before that were reached in the months of February 2024 and December 2023 signifying the constantly growing adoption of Harden-Runner.
StepSecurity Harden-Runner provides network egress control and CI/CD infrastructure security for GitHub-hosted and self-hosted runner environments. It has been leveraged by Microsoft, Google, CISA, DataDog, Intel, and hundreds of other organizations to enhance their GitHub Actions security.
How StepSecurity Harden-Runner Helps You Prevent CI/CD Supply Chain Attacks
Harden-Runner is designed to help you seamlessly detect and prevent CI/CD supply chain attacks like the XZ Utils and SolarWinds incidents.
Here are the key threats Harden-Runner defends your workflows against:
- Exfiltration of CI/CD Secrets and Source Code: Most CI/CD supply chain attacks exfiltrate the source code or sensitive CI/CD secrets from CI/CD pipelines. Harden-Runner monitors and blocks egress traffic at the DNS and network layers. This ensures that there is no exfiltration of code and CI/CD credentials, thus preventing Codecov-style CI/CD security attacks.
- Tampering of Release Builds: Another attack approach is tampering of source code during the build process to inject a backdoor. Harden-Runner detects if the source code or a build artifact is being tampered with to prevent such supply chain attacks.
Here are all the Harden-Runner capabilities that will enable you to secure your workflows from supply chain attacks:
- Real-time Monitoring: Harden-Runner continuously monitors file and network operations during CI/CD pipeline execution for unusual activities. You can view the outbound traffic for each job. The outbound network call is correlated with each step of the job after the workflow is complete. In addition, you can also detect suspicious source code and build artifact overwrite operations in software build and release pipelines.
- Anomaly Detection: Harden-Runner identifies deviations from the expected build behavior and flags potential anomalies. The expected build behavior is formed from the first few runs to form a baseline. Any new outbound destinations after this are marked as anomalous.
- Detailed Insights: Harden-Runner provides comprehensive reports and insights into the build process, helping to pinpoint the exact nature and source of the issue. This means Harden-Runner can also detect source code overwrites and send you an alert in real-time for the same.
InstructLab Includes Harden-Runner in Their GitHub Actions Use Policy
Harden-Runner was recently included in the GitHub Actions use policy of the InstructLab project. Created by IBM and Red Hat, InstructLab provides a cost-effective solution for improving the alignment of LLMs and opens the doors for those with minimal machine learning experience to contribute. InstructLab is a model-agnostic open-source AI project that facilitates contributions to Large Language Models (LLMs). They focus on creating interactive and engaging educational experiences by leveraging the power of GitHub and open-source tools. Here’s what they have to say about Harden-Runner in their policy:
“To further increase security, the first step of each job in a workflow must be the step-security/harden-runner action. This action hardens the action runner by implementing network egress control and some infrastructure security.
Each execution of the workflow job will produce a report showing endpoints accessed by the job and possible source file overwrites. The report will also suggest modifications to the harden-runner action's configuration to further increase security.
Hardening the action runner like this can prevent malicious or misbehaving actions or the misuse of actions from exfiltrating secrets.”
Explore InstructLab’s GitHub Actions Use Policy here: https://github.com/instructlab/dev-docs/blob/main/docs/github-actions-use-policy.md
New Harden-Runner Features
In the past two months, we released the following new enterprise features:
Calculating Minimum Token Permissions using outbound GitHub API Calls
StepSecurity Harden-Runner can now monitor outbound HTTPS requests using eBPF. This feature helps detect and block the exfiltration of CI/CD credentials and recommends the minimum GITHUB_TOKEN permissions required for each job in your workflow. By analyzing the PATHs and VERBs of HTTPS calls, it provides insights into the minimum token permission, enhancing security and minimizing unnecessary access. In the screenshot below, you can see examples of outbound HTTPS requests and how these HTTPS calls were used to calculate the minimum token permission:
- The GET request to the /repos/org/repo/actions endpoint requires the "actions: read" permission.
- The PUT request to the /repos/org/repo/code-scanning endpoint requires the "security-events: write" permission.
- The GET request to the /repos/org/repo/info/refs?service=git-upload-pack endpoint requires the "contents: read" permission.
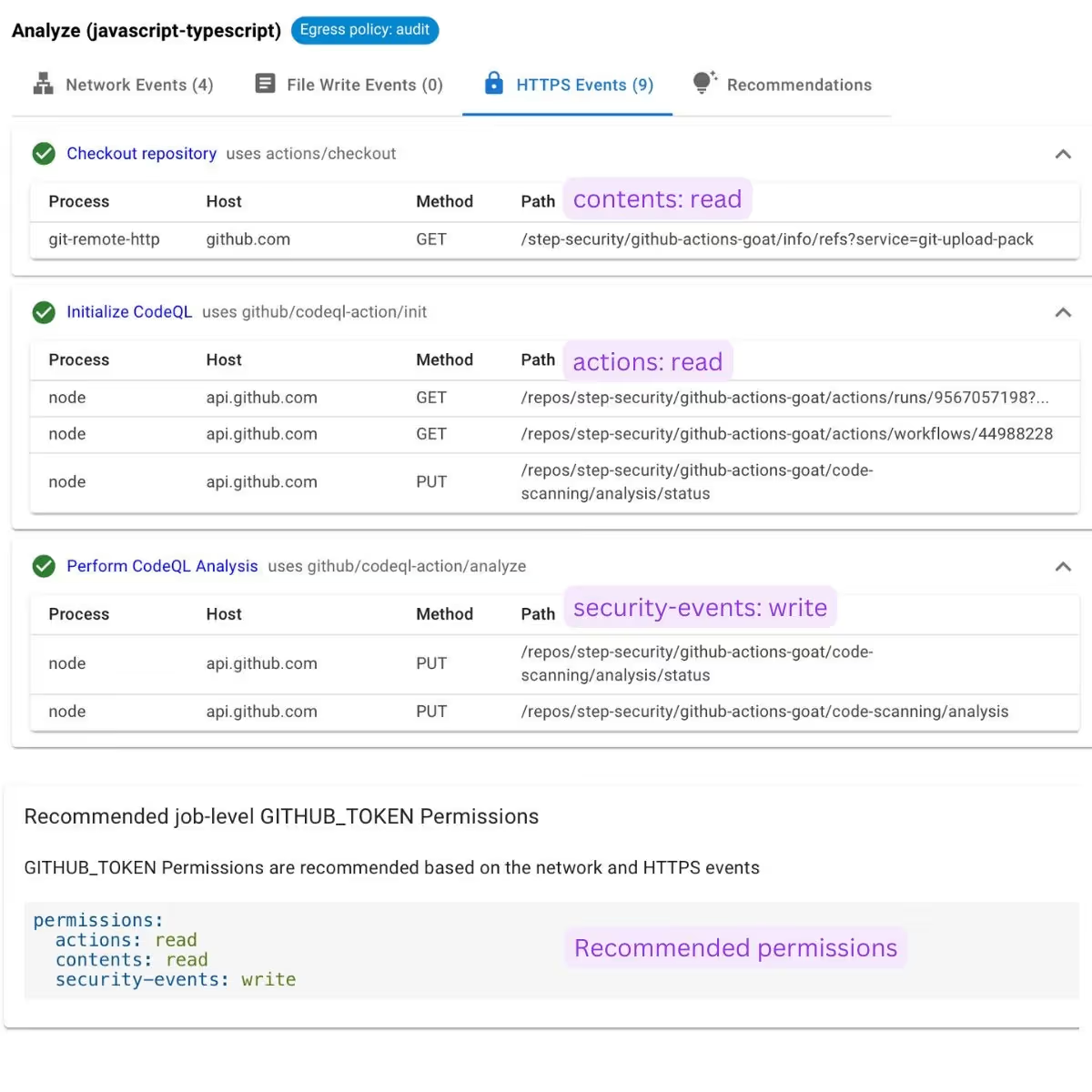
StepSecurity uses the PATHs and VERBs of these HTTPS calls to recommend the minimum GITHUB_TOKEN permissions for each job in your workflow.
Source code files, dependencies, and build artifacts created/downloaded during workflow runs
Earlier Harden-Runner flagged overwritten source code files and build artifacts. This is helpful to detect XZ Utils and Solarwinds style CI/CD security attacks where a backdoor in injected into the software binary during the build process.

We recently improved this feature for enterprise customers to show all source files and dependencies that are downloaded locally on the runner. Harden-Runner also shows all build artifacts that are generated during the workflow run. In addition, for each such file, now our enterprise customers can see which process created the file and traverse the process tree along with command line arguments for all the processes. This can be used to create a Software Bill of Materials (SBOM) for a software binary using the runtime events.


Expanding Support for Harden-Runner Beyond GitHub Actions

At StepSecurity, we’re constantly looking to expand our security solutions and are looking forward to extending our security solutions for CI/CD platforms beyond GitHub Actions! We are currently in the process of extending Harden-Runner to support GitLab, BitBucket, Azure DevOps, and Harness. If you are using one of these CI/CD providers and are interested in enhancing your pipeline security with Harden-Runner, we would love to hear from you. Please reach out to us at https://www.stepsecurity.io/contact.
Try Out StepSecurity Harden-Runner
If you haven't yet tried Harden-Runner, now is the perfect time to join the thousands of developers who have already benefited from our solution. Let us secure your repositories from the ever-evolving supply chain attacks while you focus on building amazing software!
Thank you for being part of our journey. Here's to securing the next 3500 repositories and beyond!


.png)
.png)

